Penetration testing is the most important job in the world of security. Many online platforms allow users to practice their penetration testing skills. Hack The Box is one of them. It is primarily an online platform to examine and improve your abilities in penetration testing and cybersecurity. It includes various challenges that are regularly modernized. Some of them resembling real-world situations and some of them inclining more towards a CTF technique of challenge. Let’s take a look at how to join this website.
Penetration testing gives a precise report that shows the vulnerabilities that were abused by attackers. For example, how long the attacker was capable to remain unidentified, and the delicate data disclosed. This data is utilized to eradicate vulnerabilities and increase the defense of the website or mobile applications to help defend against real possible attacks.
Hack The Box also has the Pro labs. For example, RastaLabs is a virtual red team setting, created to be attacked as a method of training and sharpening your combat abilities. The focus of the lab is working within a Windows Active Directory setting where members must get a space, raise their perquisite, be determined and go parallel to attain the purpose of Domain Admin. The lab emphasizes a blend of engaging misconfigurations and affected users. Previous experience is not rigidly expected to strike the lab, but it is a sheer knowledge curve!
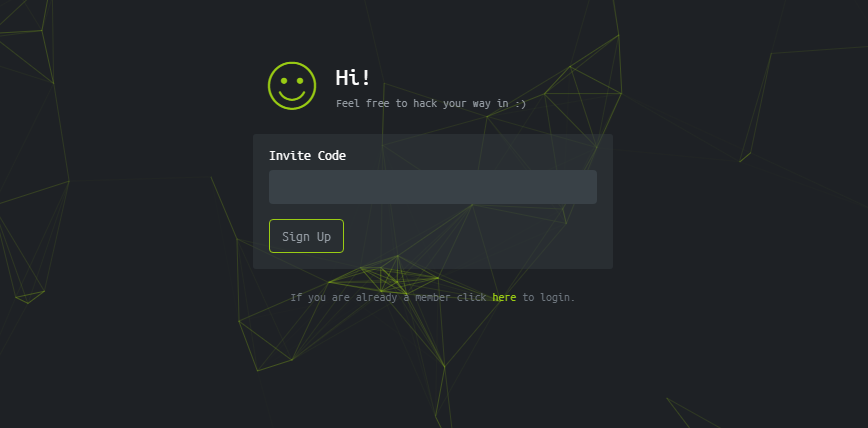
There is no normal Sign up page on this website. This is a real challenge for all users. If you want to join this website then you have to join it by hacking in. Sounds interesting?
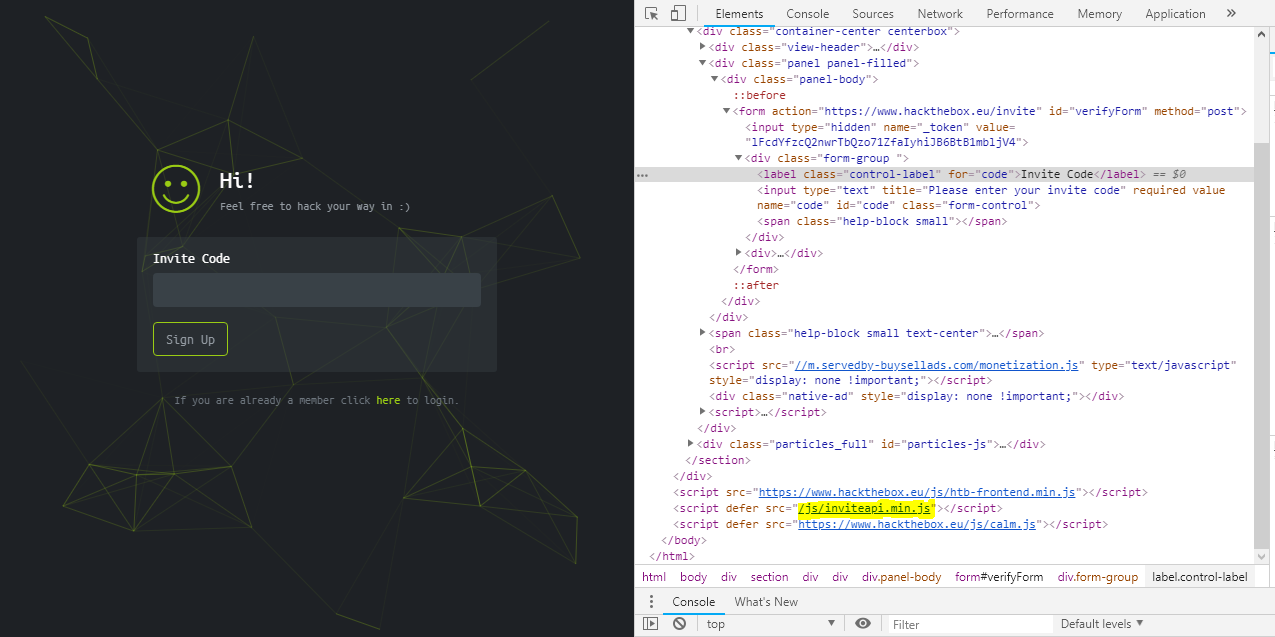
First, go to the Hack the Box website. When you visit that page, you will notice a text box requesting you for an invite code. Now the next step is, just right click on the page, and then open the inspect element. You can also press Ctrl+Shift+I to initiate the Chrome Developers Tools. Now, check the elements tab. Here you will see a script source: /js/inviteapi.min.js as displayed in the below figure:
Now go to https://www.hackthebox.eu/js/inviteapi.min.js and you will notice a JS file.
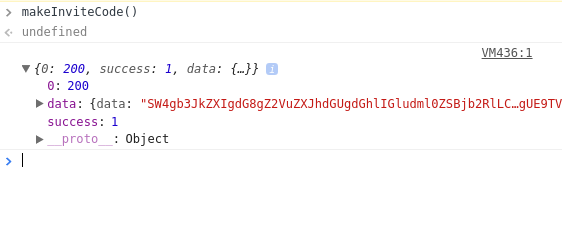
With this new knowledge, now again visit https://www.hackthebox.eu/invite. Now we aim to discover the contents of makeInviteCode. For doing this, just go to the Console tab and insert makeInviteCode() and press Enter. You will see a 200 Success status and data as displayed below:
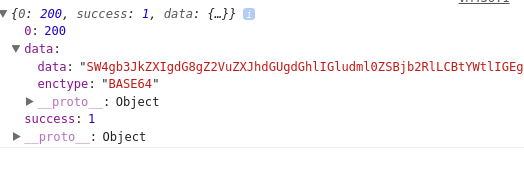
Now click the small arrow beside data, you will notice the encoding Base64 as displayed below:
Now, the next step is to decode this message to get the necessary data. For this, copy the data. You can decode this data by using many free online Base64 Decryptor. Paste the copied data in one such online decryptor and click DECODE.
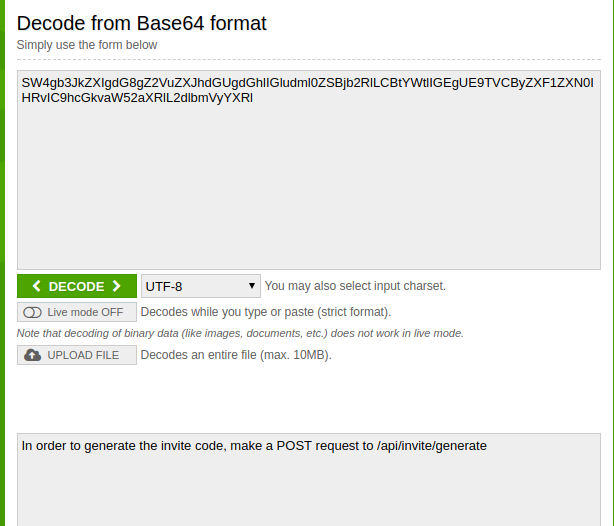
Now to get the invite code, you have to make one POST request to https://www.hackthebox.eu/api/invite/generate. To do this, open the prompt and type curl -XPOST https://www.hackthebox.eu/api/invite/generate. After this, you will get the success message. One thing to remember here is that this is not the invite code. You still have to decode the encrypted message. To do this, go to https://www.base64decode.org/ and paste the code you got as the output of the POST request into the textbox. This will be your invite code.
Now, go to https://www.hackthebox.eu/invite and paste the Invite Code you received in the textbox. That’s it. You are in.
The observation stage is the most critical phase of the hacking methodology. You can never win a battle if your reconnaissance ability is weak. The value of reconnaissance is to collect valuable data and details about the chosen destination. This data can then be utilized in the field, to reach the possible permanent location.
The process includes penetrating for vulnerabilities as well as giving the testimony of speculation attacks to reveal the vulnerabilities are visible. Proper penetration testing permanently ends with appropriate suggestions for addressing and fixing the difficulties that were found during the study. In other words, this process is used to enhance the security of the rules against growing assaults. The overall objective is to fix security problems by using a special methodology, tools, and procedures as an attacker. These results can then be reduced before a true hacker abuses them.